Detect And Remediate - Zero-Day Vulnerability Attacks

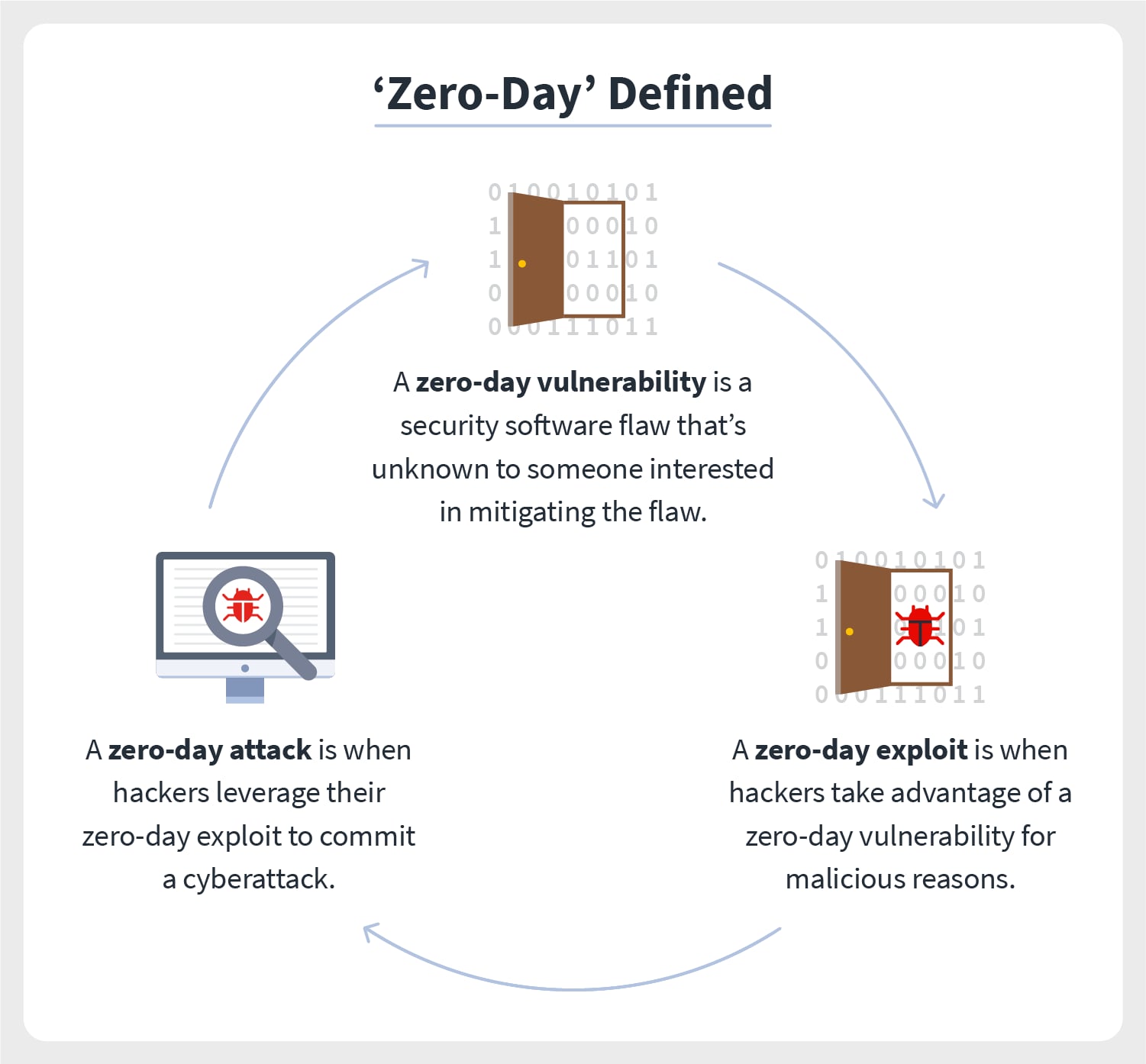
Before you know it, Zero-Day Vulnerabilities will get exploited by hackers and cost you unprecedented losses. Cyber attacks using a zero-day vulnerability are becoming more common and dangerous. The threat posed by undiscovered or unfixed security flaws in software or apps is "zero-day." These malicious codes exploit undetected code vulnerabilities before they are known to the developers or security analysts. Therefore, attacks that leverage zero-day vulnerabilities frequently occur without users being aware of them; this can result in significant financial losses for enterprises due to lost productivity, data theft, system outages, reputational harm, and legal actions.
When a hacker or cybercriminal discovers a zero-day vulnerability in any software, they are more likely to look for ways to exploit it than to alert the developers. These resulting zero-day exploits are offered for sale on the dark web. Anyone willing to pay the correct price can utilize insecure software to steal money or data from computers, then use that information for their gain. One such example is a hacker selling cybersecurity exploits as an NFT.
The prevalence of cyber dangers is increasing along with the use of technology. A magazine claims that the black net has around 300 cyber threats every week. According to the team of Project Zero-day by Google, in the year 2021, the highest number of zero-day attacks occurred, discovering 58 vulnerabilities. Let's examine a zero-day vulnerability attack, how it operates, and how to stop one.
What Is A Zero-Day Attack?
A zero-day attack happens when a hacker exploits a hardware or software flaw the developer is unaware of. The victim has "zero days" to prepare for it because it can happen abruptly and without notice, hence called "zero-day."
Why Is The Number Of Zero-Day Attacks Increasing So Rapidly?
The rise of zero-day attacks can be attributed to a variety of factors. The rising value of digital assets is one factor that makes hackers more eager to access data. For instance, the 200 million dollars in value locked up in just the DeFI projects makes them a lucrative target for hackers. Large amounts of money in the form of bounties are given to hackers in exchange for their help in stealing data from various businesses and people, giving hackers even more incentive to use zero-day vulnerabilities. Another factor is the improved quality of open-source tools designed for use in development.
What Are The Best Methods For Preventing Zero-Day Attacks?
Since zero-days are so challenging to forecast and prevent, some of the traditional methods that have been the primary approach to dealing with them.
Vulnerability Scanning
Zero-day exploits can be found through vulnerability detection. BlockChainSentry provides vulnerability scanning tools to evaluate code and look for any new vulnerabilities that may have appeared after a program update.
Patch Management
Another method is to deploy software patches as quickly as possible for recently identified software vulnerabilities. While this cannot stop zero-day attacks, it can dramatically lower the risk of an attack by swiftly installing patches and software upgrades.
Web Application Firewall
Installing a web application firewall will enable your business to respond to attacks instantly. A web application firewall continuously checks incoming data for risks, giving companies the knowledge to take action and overcome an oncoming attack.
Zero-Day Initiative
The zero-Day Initiative program can be designed to encourage security researchers to report vulnerabilities ethically rather than selling the data on the black market. This will motivate establishing a sizable community of vulnerability researchers who can find security flaws before hackers and notify software makers about them.
How BlockChainSentry Detects Zero-Day Vulnerabilities
The BlockChainSentry Vulnerability management platform is well equipped with zero-day vulnerability detectors. It can scan publicly known vulnerabilities of SWC and CWE; our detectors can scan and identify more than 110+ vulnerabilities, including conformance and operational vulnerabilities. BlockChainSentry gives you the flexibility to detect vulnerabilities that are required for rule-based compliance. It can ensure that all the processes of smart contract development are followed and comply with the specific requirements, along with managing all code vulnerabilities.