What is Cryptography in Blockchain?
With the ability to incorporate consensus processes, distributed data storage, digital encryption technology, peer-to-peer transmission, and other computing technologies, blockchain has emerged as one of the most inventive application models. It has given rise to an efficient platform for the secure, decentralized exchange of information. The fundamental components of blockchain technology are digital encryption techniques, which emphasize the importance of blockchain cryptography. Find out what role cryptography plays in blockchain technology. How secure is blockchain, and what are the attributes of blockchain security?
Evolution of Cryptography
The word cryptography is derived from Kryptos, a concealed word in Greek. Only the sender and intended recipient of a message can access the contents of that message through a secure communication method known as cryptography. It is closely related to encryption, which converts plain text into ciphertext before sending it and then back again after receiving it. The obscuring of information in photographs using methods like microdots or merging is also covered by cryptography. The ancient Egyptians employed these techniques in their intricate hieroglyphs, and Julius Caesar, the Roman Emperor, is credited with creating one of the earliest modern ciphers.
Role of Cryptography in Blockchain?
Blockchain technology was created using various cryptographic ideas; what blockchain gains from cryptography are as follows,
Security
The blockchain ledger's security depends on cryptography. Cryptography is mainly used for protecting user privacy, transactional information, and data consistency. On the blockchain, each transaction is recorded using encrypted data. With the use of their public and private keys, each user has secure access to their data and can purchase and sell cryptocurrencies.
Blockchains use cryptographic hashing to store root hashes that securely encode each transaction. An entirely different hash will be generated at the root hash if someone attempts to alter any data in the blockchain. Other users can determine that the data is hacked by comparing that root hash to its on their computer.
Scalability
An endless number of transactions can be securely stored over the network via cryptographic hashing. Blockchains can keep expanding at scale because several transactions can be combined into a single hash.
Reliability
Since cryptographic hashing is irreversible, transactions cannot be reversed. They are protected from any hostile activity, which also ensures that all users may rely on the accuracy of the digital ledger.
Types of Cryptography in Blockchain
Blockchain employs key cryptography to protect the information from assault and unauthorized use and to ensure the sender and receiver's identities. Key cryptography can be divided into two categories based on the number of keys used by the nodes to conduct a safe exchange of information between them, known as Symmetric cryptography and Asymmetric cryptography.
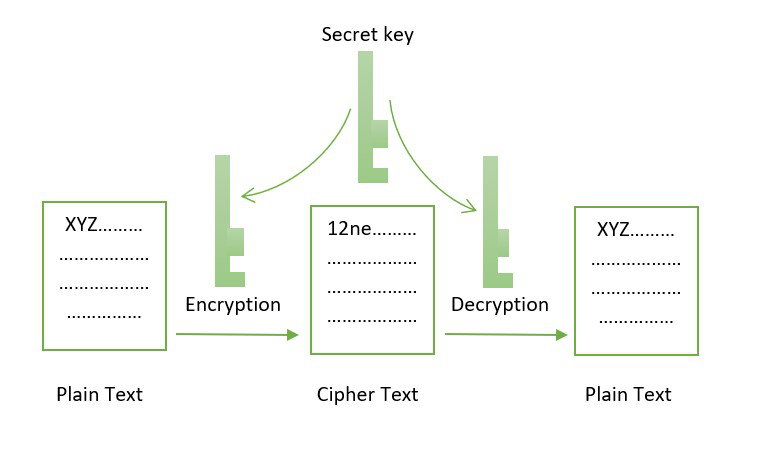
Symmetric Cryptography
The symmetric cryptography method was the first key cryptography implemented in a blockchain network. Both nodes, in this manner, encrypt and decode data using the same key.
Let's say Node A requests that Node B receive some sensitive information. Node A will use key k1 to encrypt the data into an unintelligible ciphertext and deliver it to Node B to enable this transition using the symmetric key approach. Using the same key, k1, Node B will receive the ciphertext and decrypt it. This indicates that the key k1 must be the same for both Nodes A and Node B.
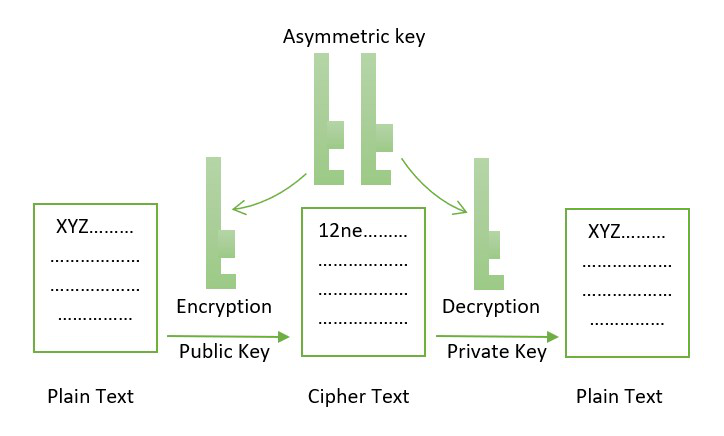
Asymmetric Cryptography
Asymmetric cryptography does not require two nodes to share the same key. An alternative is that a node has two keys: a private key and a public key. These keys always come in pairs because they cooperate. In other words, we encrypt the message with the public key and decrypt it with the associated private key. Digital signatures employ this technique to ensure that the blockchain is valid and the data is verified and correct. It uses digital signatures for verification in every recorded transaction, the sender signs the transaction with a digital signature to ensure data is not corrupt.
Let's imagine Node A needs to transfer Node B sensitive data, such as bank account information. Now, Node A will encrypt the content twice, once by using its private key (A) and once by using B's public key. When this text is encrypted, Node B will decrypt it using its private key, B, and then again with A's public key.
Cryptographic Hashing
Another essential component for safeguarding the blockchain and making it unchangeable is hashing. The process of encoding the data or information on a blockchain into an unreadable, uncrackable language is known as cryptographic hashing. This is accomplished using the SHA-256 hashing technique, a unique type (Secure Hash Algorithm) that produces a 32-byte long hash value.
The hash is always a fixed length, no matter how long the input value is. However, the same hash values cannot be used for various inputs.
Final Thoughts
The basis on which blockchain is constructed is cryptographic technology. With cryptography, we can encrypt data, send cryptocurrency securely, and keep track of past transactions. It guarantees that blocks will keep being added to the chain without end and enables us to trade cryptocurrency safely without the need for a centralized authority.
Blockchains can hold enormous amounts of transactions and keep those transactions safe from hackers with cryptographic hashing. It secures, validates, and scales online transactions. In other words, blockchain is secure and immutable because of cryptography.