Blockchain Trilemma and Scalability
Blockchain applications strive for three objectives - Decentralization, Scalability, and Security, all simultaneously, but getting the right balance between the three is the “Blockchain Trilemma.” This term is coined by Vitalik Buterin, which is a challenge for every blockchain developer working on DApps. One or the other gets compromised to achieve the right balance between these three aspects. If we work on making the blockchain project more secure and scalable, they will be more centralized, and if we keep fewer nodes on the blockchain to increase scalability, transaction speed, security, and decentralization gets compromised. Does that mean achieving the right balance between these three objectives is very difficult!, this is what we will discuss in this article….
Blockchain Trilemma
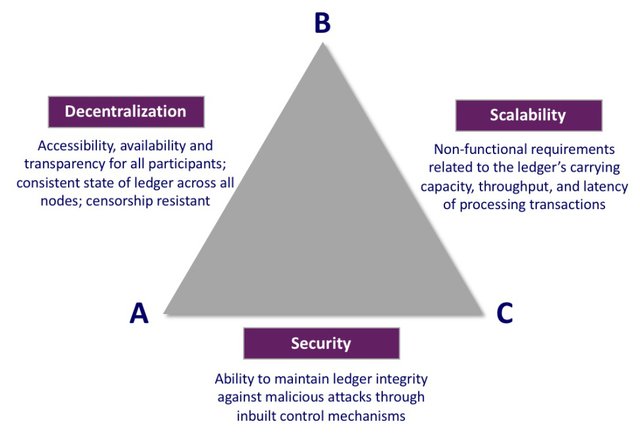
Source: https://steemit.com/blockchain/@reverseacid/the-scalability-trilemma
Layer 1 solutions are the main blockchain networks such as Ethereum and bitcoin, these are more decentralized and secured, but the limitation of Layer 1 networks is scalability. Layer 2 networks are created to complement the scalability of the Layer 1 networks. Blockchain's integrity is preserved, scalability and higher throughput are made possible, and complete decentralization, transparency, and security are enabled through the Layer 2 protocols, which run on top of the underlying Layer 1 blockchain network.
As blockchain technology is getting adopted at a massive level, the demand for scalability is increasing with the increased demand for blockchain applications. Before we get into how the blockchain trilemma is achieved with the combination of layer 1 and layer 2 protocols, let's go a little deep down in understanding these scaling solutions.
Layer 1 Blockchain
Layer 1 solutions serve as the foundation of a blockchain network. A public decentralized Layer 1 network consensus method is an essential characteristic. Different consensus mechanisms provide varying degrees of throughput, speed, and security. The layer 1 blockchains process and log transactions in their ecosystems. They have a built-in cryptocurrency often used to cover costs and offer extra features. Bitcoin, BNB Chain, or Ethereum are the frequently used Layer 1 blockchain networks.
Limitations of Layer 1 Blockchain
All transactions in a Layer 1 blockchain are validated after being verified by numerous nodes. The so-called mining nodes compete with one another to solve a challenging computational challenge, and the winners are rewarded with the native coins of the network.
In other words, before miners can validate a transaction, it must first pass the independent verification of many nodes. This is a productive approach to log and storing accurate, validated data on the blockchain while reducing the danger of attack from malicious parties. However, the throughput demand becomes an ever-growing problem once you have a network as well-known as Ethereum or Bitcoin. Users experience longer wait times for transaction confirmations and higher transaction costs due to network congestion.
How does Layer 1 Blockchain Work
There are several ways to boost throughput and total network capacity in layer 1 blockchains. To increase the scalability of layer 1, scaling solutions work to strengthen the infrastructure underpinning the blockchain protocol. The two most well-liked Layer 1 blockchain protocols are,
Consensus Protocol
A blockchain network's core consensus protocol provides a precise way of determining whether a transaction is genuine or false. It offers a way to verify and confirm the information that should be included in a blockchain's record. Blockchain networks often lack a central authority that decides who is right or wrong. Therefore all nodes on a blockchain must concur on the network's state while adhering to the protocol's set rules. Proof of Work (PoW) consensus is used by Layer 1 blockchain to authenticate nodes and record transactions.
Sharding
A well-known layer-1 scaling method for boosting transaction throughput is sharding. The technique is a sort of database partitioning that can be used with distributed ledgers on blockchains. A network and its nodes are split into shards to disperse the burden and increase transaction speed. Each shard manages a portion of the activity on the network. This indicates that it has its blocks, nodes, and transactions. In addition to providing quicker transaction rates, the split of the network and its nodes helps efficiently allocate the burden.
In the case of sharding, each node does not have to maintain a complete copy of the entire blockchain. On the other hand, nodes exchange the status of local data, such as accounts for finished work, and report completed work to the main chain.

Source: https://blockchain-comparison.com/blockchain-protocols/
Layer 2 Blockchain
Layer 2 networks are constructed on top of other blockchains and are concerned with integrating third parties into the blockchain network's mainnet. Layer 2 solutions rely on additional networks that operate independently or concurrently with the primary network. For example, the Lightning Network is a Layer 2 and runs on top of Bitcoin (which is a Layer 1).
How does Layer 2 Blockchain Work?
Rollups
The most popular type of zero-knowledge rollups combine off-chain Layer 2 transactions and submit them as a single transaction to the main chain. These systems use validity proofs to validate the accuracy of transactions. A bridging smart contract is used to hold assets on the original chain, verifying that the rollup is working as intended. This combines the advantages of a less resource-intensive rollup with the security of the original network.
Sidechains
Blockchain Sidechains are separate networks with their validators. The main chain's bridge smart contract does not independently confirm the legitimacy of the sidechain network. As a result, the sidechain can manage assets on the main chain.
State Channel
It is a two-way communication channel between the parties involved in the transaction. The parties connect an off-chain transaction channel to a section of the underlying blockchain that is sealed off. Typically, a multi-signature or a pre-negotiated smart contract is used to do this. Without immediately uploading transaction data to the underlying distributed ledger, the parties then carry out a transaction or a sequence of transactions off-chain. Once all transactions in the set have been completed, the channel is broadcasted to the blockchain. This method enables faster transaction processing and boosts the network's total capacity. Ethereum Raiden and the Bitcoin Lightning Network use the state channel model
Nested blockchains
This approach is based on several supplementary chains built on top of the primary, or "parent," blockchain. Nested blockchains function under the constraints and guidelines established by the parent chain. The main chain's involvement in transaction execution is minimal and only serves to resolve conflicts as they arise. The daily operations are assigned to "child" chains, which return the completed transactions to the main chain upon completion. Layer 2 nested blockchain technology is used in OmiseGO's Plasma project.
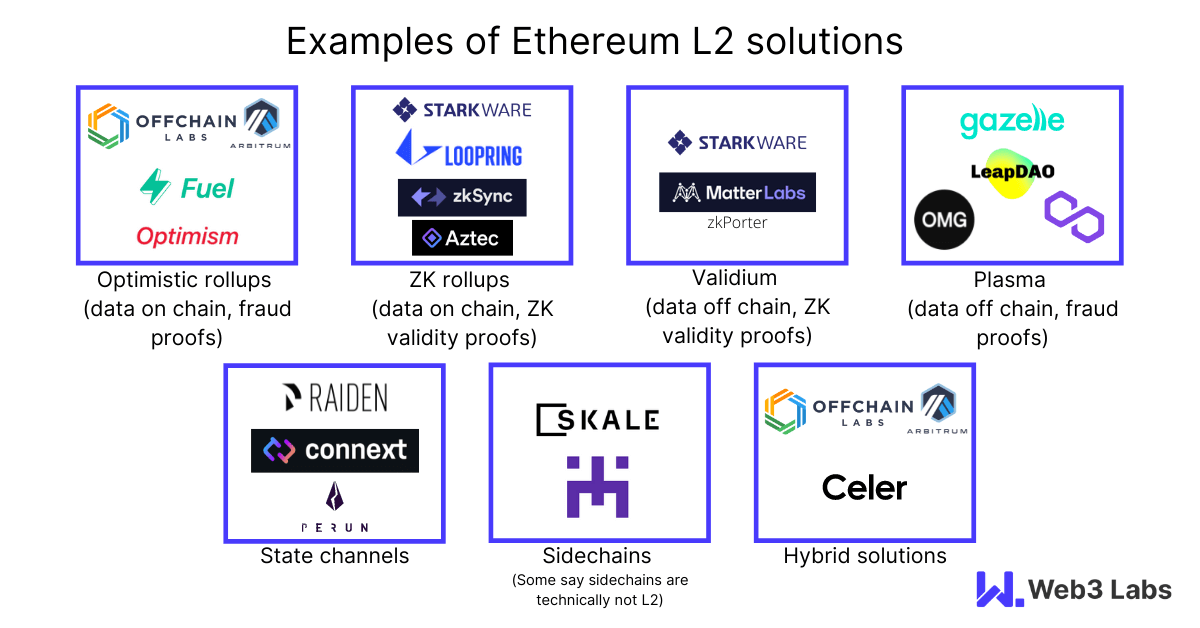
Source: https://blog.web3labs.com/scaling-the-ethereum-network-a-primer-on-layer-2
Layer 1 blockchains rely on layer 2 networks to fulfill the third aspect of Scalability, still, there are many concerns regarding transaction fulfillment from layer 2 to layer 1, cross bridge vulnerabilities, and other complexities of network bridging for end-users. Layer 1 and Layer 2 solutions each have specific benefits and drawbacks. Currently, existing blockchains with good scalability include polygon and quorum, which are layer 2 EVM networks.
Ethereum is claiming to increase its scalability with the launch of Ethereum 2.0, but it will take time. However, the base concept of Layer 1, which focuses on security while letting Layer 2 networks customize their services for specific use cases, will be the definite structure of this technology. Large chains like Ethereum will continue to rule due to their sizable user and developer communities, even if there is a good likelihood that many competitors will emerge soon to create the best method for scaling a greater throughput.
With this complex structure of layer 1 and layer 2 combinations, the users can manage to achieve Blockchain Trilemma to a large extent, but this solution still creates lots of loopholes for vulnerabilities to enter into the blockchain network. Considering comprehensive vulnerability management platforms like BlockChainSentry VMS that offer security products and solutions for all EVM layer 1 and Layer 2 applications can curb these vulnerabilities and exposure to cyber-attacks to a large extent. BlockChainSentry platform not just detects and remediates more than 110 vulnerabilities at multiple touchpoints but also offers services like security audits of DApps, Threat intelligence, and penetration testing services for the client. Contact us if you are looking for a one-stop blockchain security solution company.