Hashing in Blockchain?
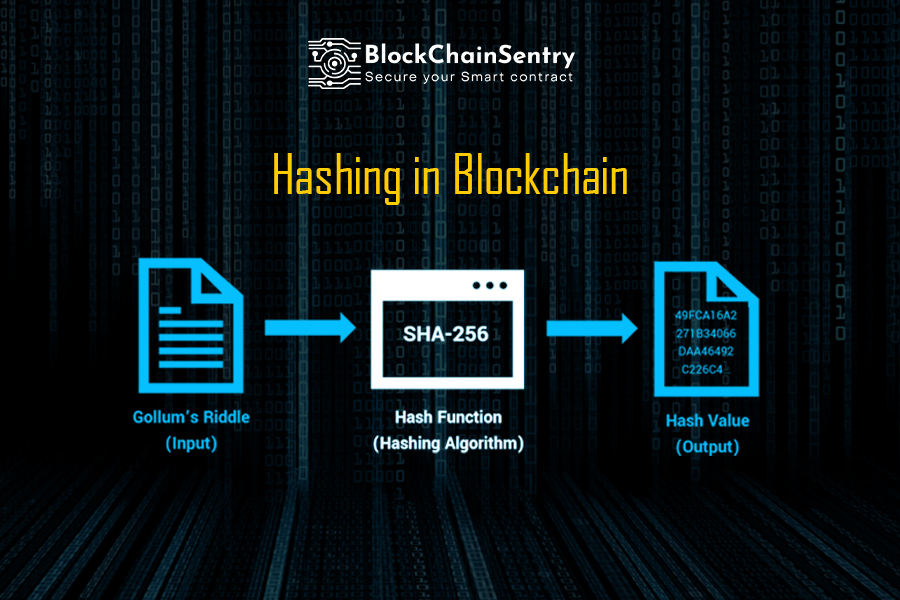
The holy trinity of blockchain technology consists of distributed computing, mechanism design, and cryptography algorithms. As we discussed in our earlier blog post, blockchain security is provided by cryptography. The blockchain uses a cryptographic hash algorithm to link each block in a chain to protect the message block. In the blockchain, each block hash and the hash of the block before it help to create a linear chain of blocks that is cryptographically safe. This blog will describe the characteristics of cryptographic hash functions and how they are employed in blockchain to safeguard your communication.
Hashing
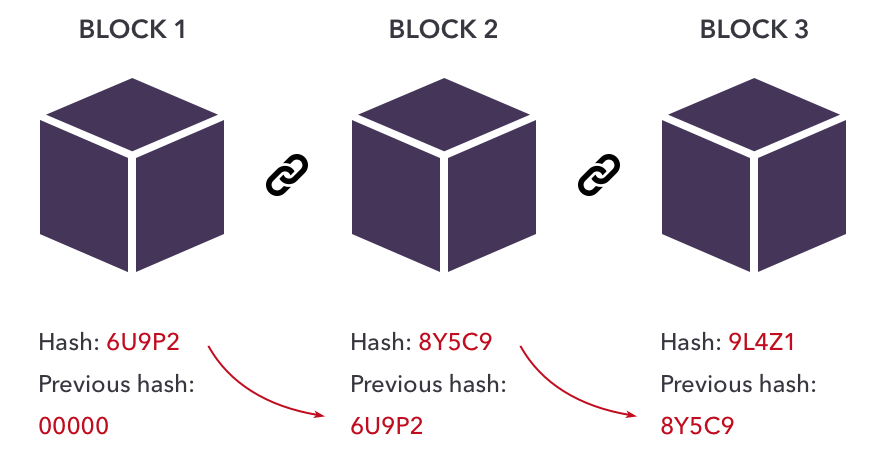
Blockchain hashing turns an input item of any length into an output item of a specific length. If we utilize blockchain technology, transactions of different durations are processed using a particular method of hashing, all producing results with a defined length. Regardless matter how long the input transaction is, this is true. The result is what we refer to as a hash. Bitcoin's Secure Hashing Algorithm 256 (SHA-256) is an excellent illustration. When employing SHA-256 for hashing, the output result always has a set length of 256 bits (the output is 32 bytes). This holds regardless of the transaction's complexity or whether it involves a small number of words or a sizable amount of data. This indicates that it is simpler to maintain track of a transaction when you can recall or trace the hash. The hash's size will vary on the hash function used, but the hash produced by a given hashing method will have a predetermined size. Thus each block in a blockchain has
- Data
- Hash
- Hash of the previous block
Uses of Hash Functions in Blockchain
Hash functions are used in many different ways on the blockchain. The hash function is most frequently used in blockchain for the following purposes:
Merkle Tree: This uses hash functions to ensure that it is impossible to locate two Merkle trees with the same root hash. Storing the root hash within the block header and preserving the transactions' integrity helps protect the block header's integrity.
Proof of Work Consensus: Creating new blocks of transactions to a cryptocurrency's blockchain is known as proof of work (PoW). Making a hash (a lengthy string of characters) that matches the target hash for the current block is the work that hashing does. This grants the cryptocurrency miner the ability to add that block to the blockchain and earn rewards.
Digital signatures: Hash functions ensure data integrity and serve as the basis for blockchain transaction authentication.
The chain of blocks: In the blockchain, each block header carries the hash of the block header before it. This makes it impossible to alter any part of a blockchain, not even a single block, without being noticed. The difficulty arises because changing one block necessitates creating new versions of every subsequent block.
Hashing Characteristics and Properties
Blockchain uses a hash algorithm that has specific distinctive characteristics. These attributes are:
- The technology gives every transaction a distinct output or hash.
- The one-way hash functions utilized in the blockchain can neither be reversed nor changed.
- The blockchain uses the cryptographic hash function's features as its consensus process. The cryptographic hash serves as both a digest and a digital fingerprint for a specific amount of data.
- The transaction is accepted as an input and runs through a hash algorithm in the cryptographic hash functions used by the blockchain to produce a fixed-size output.
Solving the hash
When the node begins "hashing" the data, it converts it into the hash value or "hash," which needs to contain a certain number of zeros. The node determines whether a hash satisfies the requirements. The correct number of zeroes must begin the hash. The network's other miners receive the hash if it satisfies the requirements. The block is converted into a new block, and the block reward and fees are paid in Bitcoin to the first miner who finds a valid hash.
Another nonce is chosen and hashed if the current hash does not satisfy the requirements. Before they locate a nonce that meets the requirements, miners will likely have to generate a lot of hashes with a lot of nonces. Bitcoin mining is a time-consuming and resource-intensive operation that demands a lot of processing power
The Proof of Work procedure's foundation is made out of hashing operations. The blockchain would not be tamper-proof and unchangeable without confirmation and the production of hash transactions, making it impossible to establish who possessed how much Bitcoin and when.
Final Thoughts
The blockchain system depends on and is built around the cryptographic hash. The integrity and immutability of data recorded on the distributed ledger are protected by the widespread usage of hash functions in blockchain technology. Ledger immutability is crucial since the ledger is stored decentralized, with each node keeping a copy. In the absence of consensus, nodes might alter their copies of the ledger for their gain.
Security of the hash function is, therefore, crucial to blockchain security. A blockchain's hash function must always remain secure, or the system's security will be compromised.