How And When Vulnerabilities Enter Smart Contracts, What Is The Way To Remediate Them?

In the past 10 years, the crypto market grew at an exponential rate and also witnessed various cyberattacks, financial losses, uncertainties around the emerging decentralized financial system in the world. Millions of ethers were lost due to vulnerabilities in the smart contracts, by DAO attack, Parity multi- sig wallet, and many other similar cyberattacks by hackers. For instance, the DAO attack resulted in the loss of about 3.6 million Ethers (valued at about US $55,000,000) in June 2016 [3]. Similar attacks such as Parity MultiSig Wallet and SmartMesh occurred in 2017. These events have changed the perception regarding the security aspects of the blockchain smart contracts on the Ethereum network. Sometimes these are actual hacker attacks on smart contracts and sometimes they could be vulnerabilities in the blockchain code while development or deployment.
Ethereum – The Eminent Blockchain Platform For Smart Contracts
Many blockchain platforms are available to develop smart contracts with their own designs: Ethereum, EOS, Hyperledger Fabric, Tron, Qtum, Cosmos, Cardano, Klaytn, ICON, etc. Amongst all these platforms, Ethereum is supposed to be the most secure and used platform for developing smart contracts. Ethereum is a decentralized, open-source platform with smart contract functionality. The platform allows anyone to deploy permanent and immutable decentralized applications onto it, with which users can interact. Ether is a cryptocurrency generated by the Ethereum protocol. Ethereum is considered safe because of its decentralized nature, peer-to-peer functioning, and public registry.
However, even after being so well designed Ethereum is still vulnerable both at the development stage as well as at various re-entry points. One of the features of Ethereum smart contracts is the ability to call and utilize code of other external contracts. Contracts also typically handle ether, and as such often send ether to various external user addresses. The operation of calling external contracts, or sending ether to an address, requires the contract to submit an external call. These external calls can be hijacked by attackers whereby they force the contract to execute further code (i.e. through a fallback function), including calls back into itself. Thus, the code execution “re-enters” the contract. Attacks of this kind were used in the infamous DAO hack.
Smart Contract Vulnerabilities
The vulnerabilities in smart contracts can enter through various ways. It could occur due to vulnerabilities in the Blockchain on which they are developed, like immutability, transparency, during sequential execution of the smart contract, the complexity in code, or human error by the developer.
The vulnerabilities can also be due to software security issues or due to the vulnerabilities in Ethereum and Solidity; they could come in through the tools used for security analysis on Dapp. as shown in the diagram below.
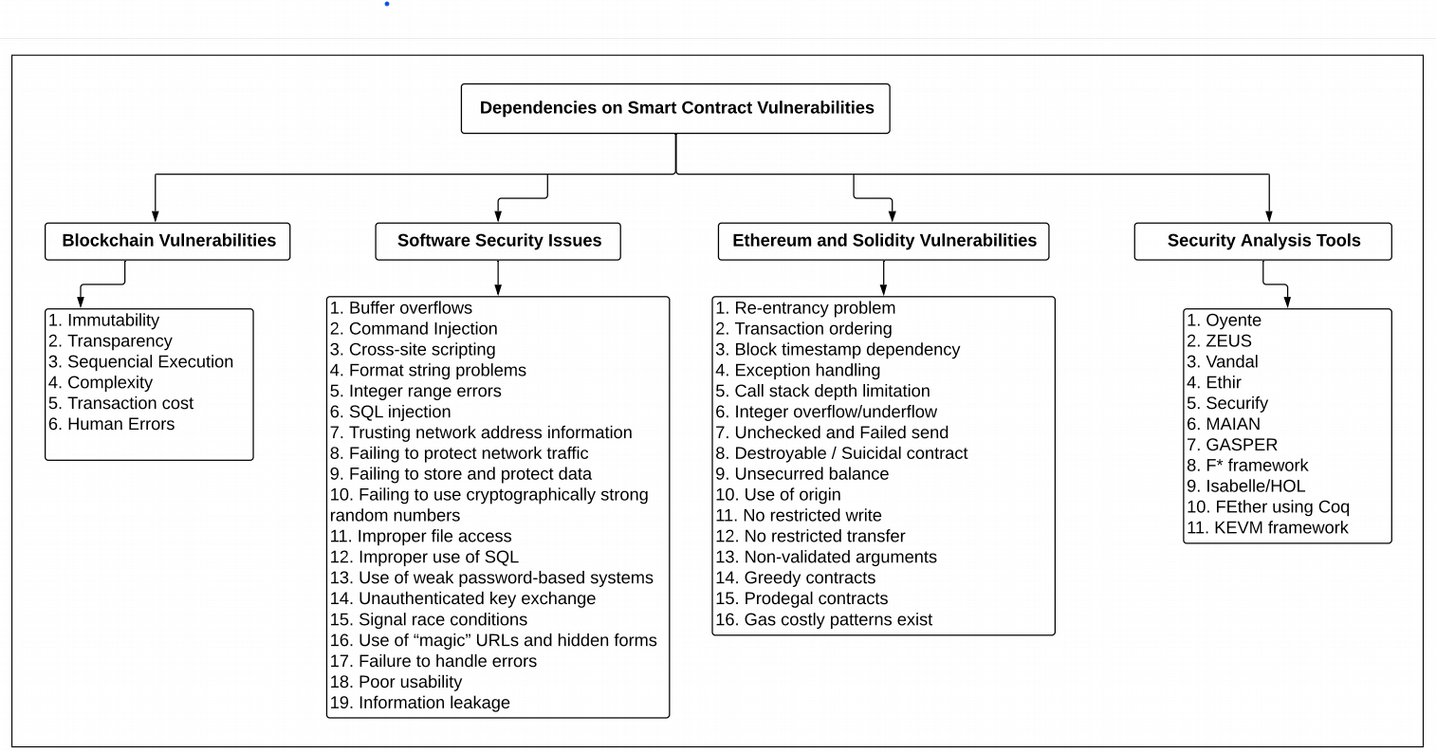
Source: Security Analysis Methods on Ethereum Smart Contract Vulnerabilities — A Survey by Purathani Praitheeshan, Lei Pan, Jiangshan Yu, Joseph Liu, and Robin Doss
Most vulnerabilities arise from weaknesses in the code. Others are re-entry vulnerabilities due to weaknesses in end-points. These vulnerabilities could occur due to their internal mechanism or due to software security vulnerabilities. The vulnerabilities in smart contracts can be detected by static and dynamic analysis and formal verification methods. The severity of the vulnerabilities can vary and the remediation for every vulnerability also could be different. As Blockchain technology finds wide acceptance in the industry, the potential cost of remediating Blockchain vulnerabilities can run into billions of dollars.
Vulnerability Remediation
Almost all the publicly known vulnerabilities on the public registry can be remediated at various stages of smart contract developments. However, the cost of remediating vulnerabilities is enormous. For remediating the vulnerabilities in smart contracts, a team of security analysts, testers, and developers constantly scrutinizes the blockchain where the smart contracts are deployed. There are not many remediation automation tools are available in the market and the one that is available requires manual testing to check the severity of the vulnerabilities. This makes the remediation process cumbersome and prone to errors.
BlockChainSentry Vulnerability Management Application
BlockChainSentry Vulnerability management application automates the smart contract vulnerability assessment process and provides immediate results of the scan on the BlockChainSentry application dashboard. This application is a state-of-the-art and scalable product that performs end-to-end continuous scanning, identifying and displaying Smart Contract vulnerabilities, also pinpoints accuracy and remediates them using Web3 technologies.
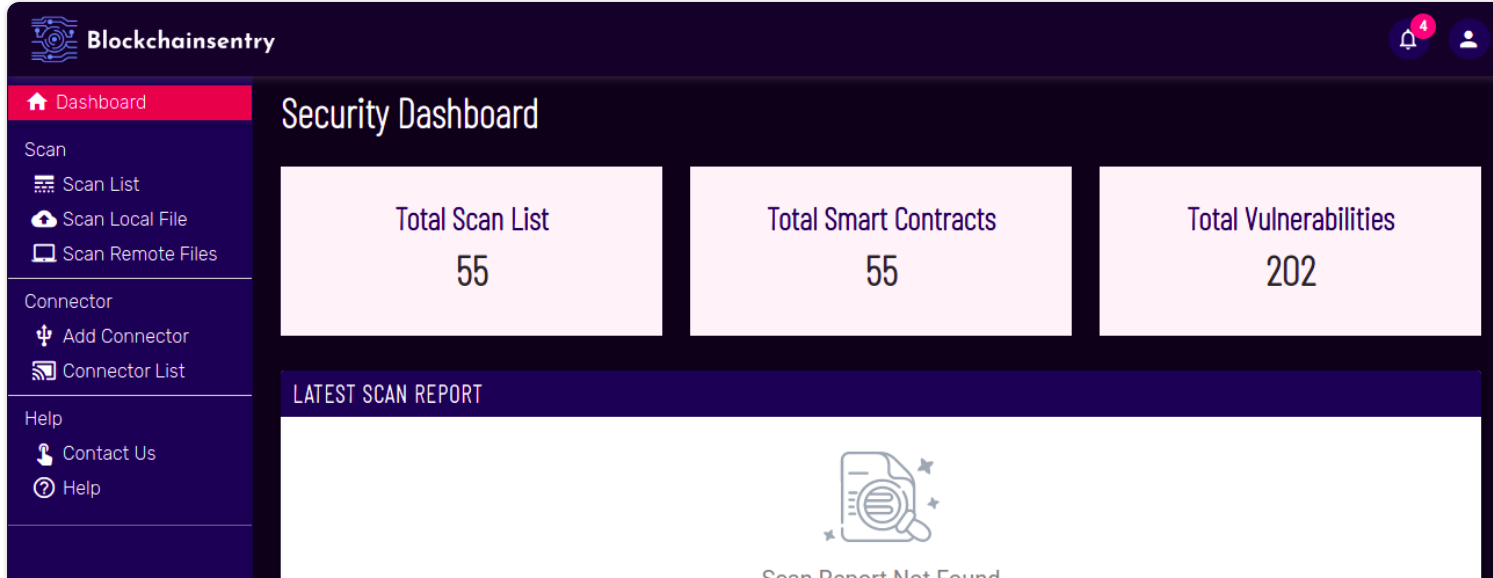
- The BlockChainSentry application has a large repository of solidity code. Any .sol file can be uploaded to this repository and scanned.
- The BlockChainSentry application sorts out the severities as low, high, or very high.
- BlockChainSentry categorizes vulnerabilities that help in prioritizing the remediation process.
- BlockChainSentry application can scan multiple smart contracts at the same time and suggest remediation.
These are some highlights of BlockChainSentry - a smart contract vulnerability management application. In the coming blog, we will talk about why is it important to shift to automation of smart contract vulnerability detection and remediation. Stay tuned!!