How Cross Chain Bridges make you vulnerable to cyberattacks?

Blockchain technology has its limitations, even if trust, transparency, accountability, auditability, and immutability are innate qualities of it. Inter-network communication and data interchange around different blockchain networks has always been an area of concern with the growing popularity of blockchain. Applications created for one blockchain network only work on that network. For instance, you cannot use ETH on BTC or BTC on ETH.
Cross Chain bridges have been used to solve this problem, and numerous initiatives have been created over time to connect blockchain networks, enabling the simple flow or interchange of data from one network to another. Polkadot, Blocknet, Cosmos, and Wanchain are notable cross-chain projects concentrating on interoperability. For instance, Blocknet focuses primarily on a decentralized exchange (DEX) between blockchains, whereas Polkadot strives to improve the flow of smart contract data between distributed platforms. Wanchain envisions a time where all digital assets coexist on a single network. At the same time, Cosmos offers a foundation for supporting additional blockchains by leveraging zones that connect to a central protocol known as the Hub. In nutshell, cross-chain bridges are connectors that can interconnect blockchain networks and help them interact with each other. Let's get into more details about this interesting topic…
What is a Cross Chain Bridge?
Cross-chain bridges are similar to an actual bridge that joins two points. It is a protocol that transfers data and digital assets among two blockchain networks, facilitating communication between them. Even though the two chains may follow different protocols, laws, and governance structures, the bridge offers secure communication between them (i.e., communicate and share data). Any data can be exchanged using blockchain bridges, including calls to smart contracts, decentralized identities, off-chain data like stock market price feeds, and much more.
Advantages of using Cross-chain bridges
Token Transfer
Each blockchain has limits because it was developed in a secure environment with its guidelines and consensus protocol. As a result, there is no token exchange or connection across blockchains. On the other hand, with blockchain bridges, it is possible to move data and coins between chains.
Reduced Traffic
Blockchain bridges reduce traffic on crowded blockchains like the one on the Ethereum ecosystem. The Cross-chain bridges help spread it out over other, less crowded blockchains to increase the scalability of the Ethereum network.
Better Options for Developers
Due to the Ethereum network's poor transaction processing speeds and high gas prices, especially during high traffic and congestion, developers building DApps, DeFi, and DAO projects have had a bad experience. Cross-chain bridges, on the other hand, make it possible for the same tokens to be processed on different blockchains more quickly and cheaply.
What makes Cross-chain bridges vulnerable
In recent research by Chainalysis, the Cross-chain bridges have become potential targets for North Korean-linked hackers. 13 cross-chain bridge breaches have resulted in the theft of $2 billion in bitcoin, most of which was taken this year. Hackers obtained 69% of the total money stolen in 2022 through bridge attacks.
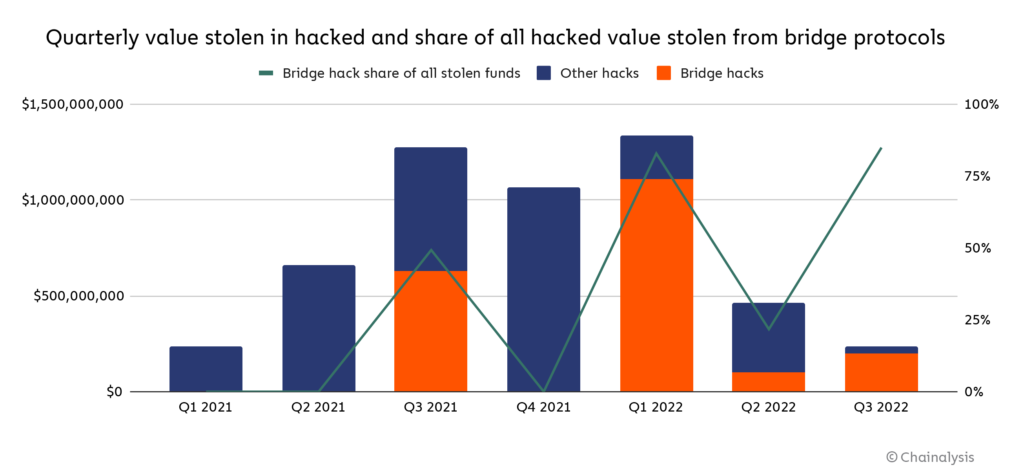
Source: Chainalysis
Blockchain bridges, which link networks to allow quick token swaps, are becoming more popular among cryptocurrency users. However, by utilizing them, cryptocurrency users are avoiding a centralized exchange and using an essentially unsecured system. Hacks and frauds have severely hurt cryptocurrency investors in 2022, and cybercriminals have discovered an efficient way to access the bridges.
Top Cross-chain bridge hacks in 2022

Vulnerabilities in all these bridges have occurred due to inadequate security and engineering practices. For instance, the low number of validators needed for transaction approval made the hack on Harmony's Horizon bridge conceivable. Only two out of five accounts had to be compromised for hackers to gain the passwords required for money withdrawals.
The same thing happened to Ronin Network, to unlock the cryptography locked inside the system, hackers only needed to persuade five of the nine validators on the network to hand over their private keys.
The bridge in Nomad's case was significantly more accessible for hackers to modify. Even if there weren't enough assets stored in the bridge, attackers may enter any value into the system and subsequently extract money.
How can Cross-chain bridge hacks be prevented?
Organizations should prioritize their security protocol for fighting against such hacks. A thorough security audit could be a helpful first step in resolving issues like these. The Security audit solution provided by BlockChainSentry works as an aid to protect your DeFi projects and assist you in building a secure blockchain environment. Companies offering Cross chain bridges should invest in security measures and training. Teams working on DApps should receive training on automation vulnerability management tools for these potential threats and vulnerabilities.
Without a doubt, cross-chain bridges are a vital tool in the decentralized finance (DeFi) sector for processing cross-chain transactions, which increases scalability and decreases network congestion, but hacks like this pose a serious risk to the development of trust in blockchain technology. We can only hope that the Blockchain industry focuses more on robust security measures so that everyone may have confidence in this new field of technology.