Security of Blockchain Network Layers
Blockchain is the distributed ledger technology behind the decentralized internet that engenders trust in the environment. On a blockchain, data is stored in blocks on designated nodes where data is recorded, shared, and viewed in encrypted smart contracts. When the capacity of a block gets saturated, then the data is chained to the previous block and creates a chain-like network, hence named Blockchain.
Security of the blockchain network is a complex process. It covers risk management of blockchain networks, cyber security framework, and best practices to cover cybersecurity risk. By design, the blockchain inherits security qualities as it is based on consensus, cryptography, and decentralization and is nearly impossible to tamper.
Even so, blockchain security is not perfect. Hackers constantly work on discovering ways to manipulate blockchain vulnerabilities. Although security is built into every aspect of blockchain technology, even the most secure blockchains are vulnerable to attacks from cybercriminals. Blockchains can withstand conventional cyberattacks quite well, but hackers continually develop new techniques for compromising blockchain technology. This article discusses the various layers of the blockchain architecture and the primary attack methods for the blockchain network layers.
Blockchain Layers
A Blockchain primarily consists of five layers: the application layer, the consensus layer, the network layer, the data layer, and the hardware infrastructure layer. Every layer performs a specific job; together, these layers enable user-friendly applications on the front end and provide data management on the back end for the blockchain as a whole.
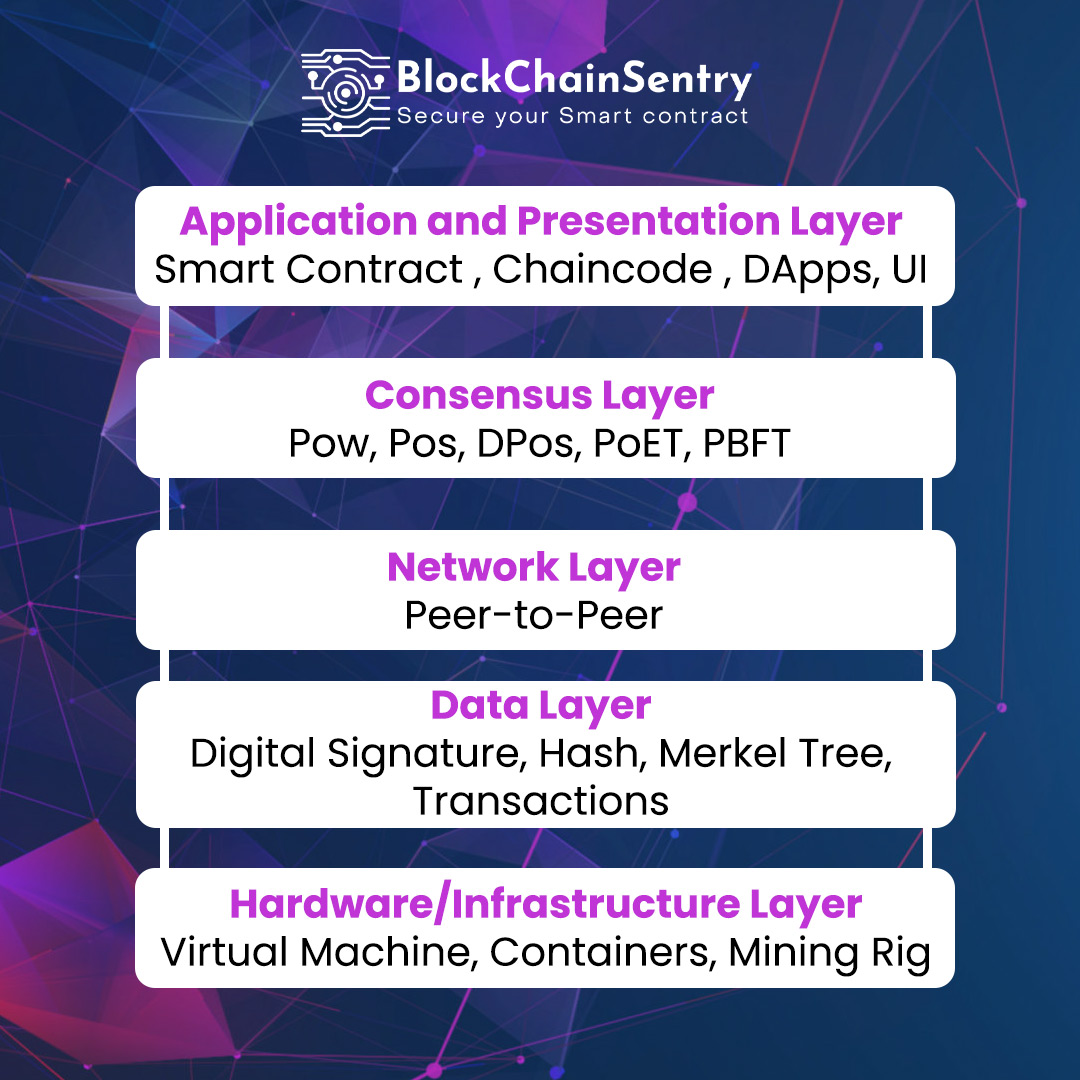
Hardware Layer
Hardware components, including network connections, computers, and data servers, make the first layer of the blockchain. Data servers house the data kept inside a blockchain, and computers connected to the blockchain network can exchange this data. As a result, a P2P network is developed in which each network node (or computer) independently verifies the information.
Data Layer
On the second data layer, the management of network-stored data takes place. Every block of information in this layer is related to the one before. The genesis block is the sole one that is not connected to any other blocks (the first block in the network). Private and public keys protect each transaction written on these blocks. A public key is used to confirm who has signed for the transaction, whereas a private key is a digital signature that is only known to its owner and is used to authorize transactions. In simple terms, to receive cryptocurrency, you must use your private key to validate the transaction and demonstrate your ownership of your blockchain wallet. Someone who wants to send you cryptocurrency will need to know your public key.
Network Layer
This layer handles the correspondence between blockchain nodes. Each node on the blockchain must be aware of the transactions other nodes are validating because it is an open system. The communication is made possible via the network layer.
Consensus Layer
This layer ensures that the network's rules are consistently upheld throughout the blockchain. To add a transaction to the blockchain, all nodes in the network must concur, one node cannot simply do this. This verification level reduces the likelihood of fraudulent transactions being added to the blockchain.
Application Layer
This layer makes it easier to use the blockchain for many different things. Smart contracts and decentralized applications (DApps) make up for it. This layer serves as the blockchain's user interface and is what a user would run into when interacting with a blockchain network.
Attack vectors on the blockchain network layers
A blockchain network consists of nodes that carry out transactions establish new ones, and offer other services. For instance, the Bitcoin network comprises miners that add authorized transactions to blocks and nodes that send and receive transactions. Cybercriminals use the following types of attacks to take advantage of network weaknesses.
Distributed denial of service(DDoS)
On a blockchain network, distributed denial of service (DDoS) assaults are challenging to carry out, but they are executed by cybercriminals. DDoS attacks aim to knock down a server by overloading it with requests, which is how hackers bring down a blockchain network. DDoS attacks target e-wallets, cryptocurrency exchanges, mining pools, and other financial services on a network. Hackers use DDoS attacks using DDoS botnets to hack a blockchain at the application layer.
The Solana network attack is one of the most well-known instances of DDoS attacks on cryptocurrency. On the Solana blockchain, a new project was introduced on September 14, 2021. This project began producing massive transactions that clogged the network with spam. It was making around 400,000 transactions per second at its peak. Transactions had to be pushed back into memory, leading to memory space becoming limited. The network crashed when it ran out of memory, resulting in a several-hour outage. After a hard fork and a network rollback were done where 80% of validators could agree, the issue was finally resolved.
Transaction Malleability Attack
A transaction malleability attack aims to deceive the target into making payments twice (double spending). Every transaction on the Bitcoin network has a hash, which serves as a transaction ID. Suppose an attacker is successful in changing a transaction's ID, then they may broadcast the transaction to the network with a modified hash to confirm it before the original transaction. If it is successful, the sender will think the initial transaction was unsuccessful, but the money will still be taken out of their account. The same amount will be deducted twice if the sender repeats the transaction. Once miners have verified the two transactions, the hack is complete.
A malleability exploit caused the Bitcoin exchange Mt. Gox to go bankrupt in 2014. The Segregated Witness (SegWit) method, which isolates signature data from Bitcoin transactions and replaces it with a non-malleable hash commitment to each signature, was the solution proposed to this problem.
Time Jacking
A potential weakness in how Bitcoin handles timestamps is exploited through time jacking. A hacker compels a node to accept an alternate blockchain by changing the node's network time counter during a time-jacking attack. Cybercriminals can accomplish this by adding numerous fictitious peers to the network with false timestamps. However, limiting acceptance ranges or utilizing the node's system time can prevent a time-jacking attack.
Routing Attacks
A routing attack might affect the network or a specific node. This hack aims to alter transactions by intercepting internet service providers (ISPs) data. It is practically impossible for other nodes to notice this tampering as the hacker separates the network into sections that cannot connect with one another. Routing attacks comprise two distinct approaches: a partition attack separates the network nodes into several groups, and a delayed attack tampers with propagating messages and transmits them to the network.
Sybil Attack
A malicious actor that makes numerous fake accounts to impersonate actual users is said to be a Sybil attack. It floods the target network with multiple fake identities to crash the blockchain network. Because of this, the system needs help figuring out how many users are on the network. However, it typically happens when a person wants to submit a transaction but wants to ensure that it is being sent on their behalf and not on behalf of an imposter. They create numerous accounts and use them all at once to carry out transactions to accomplish this. This attack aims to exploit other users by impersonating and utilizing their login information to access digital assets.
51% Attack
Unethical miners on a blockchain network try to bring enough resources to acquire more than 50% of a blockchain network’s mining capacity and gain control over the blockchain network in a 51% attack incident. Generally, this attack is made on a large-scale public blockchain network where a massive amount of mining is executed. This attack is not possible for a private blockchain network.
Eclipse Attack
A distributed botnet or extensive IP address control are requirements for an eclipse attack. The attacker replaces the addresses in the victim node's database and waits for the victim node to resume. After restarting, all incoming connections from the victim node will be routed to the attacker's IP addresses. This will give them access to an attacker from getting the transactions they want.
Final Thoughts
P2P network security and network authentication mechanisms are the key areas where the security defense for the blockchain network layer can be strengthened. A trustworthy encryption method is utilized during transmission to stop malicious attackers from stealing or hijacking the node network. Enhance the reliability, sense, and security of data transmission through networks. Client nodes should perform the necessary information and operation verification. As a leading blockchain security firm, we at BlockChainSentry provide inherent data security and effective privacy protection for all blockchain layers.